Running IT services in the cloud creates both new opportunities and risks for organizations. The cloud introduces new attack vectors that traditional PAM approaches often struggle to adequately address. This article discusses what you need to consider before implementing PAM for the cloud, and how to address the challenges you’ll face.
PAM in the Cloud vs. PAM for the Cloud
“The cloud can complicate your PAM challenges. The drive to the proliferation of privileged accounts and credentials to a state that, for most organizations, is unmanageable without processes and tools”
– Gartner
Today, security and business leaders must leverage PAM tools as well as industry best practices for comprehensive risk mitigation including protecting cloud services. Adding cloud solutions and technology to already complex access governance programs can cause IT and Security leaders to wonder if their current privileged access management strategies will work with the cloud. So, what’s so different?
For starters, we need to level set on a few concepts to help us consider PAM and the cloud in the right context.
What is the cloud?
In simple terms the “cloud” refers to accessing servers, databases, or applications hosted off-premises (not in your own datacenter). Instead, these services are accessed over the Internet, or via a dedicated network link. The datacenters that makeup the cloud are located all over the world. One of the things that makes cloud services unique is the ability to elastically scale adjusting to the demands of variable workloads.
Adding PAM to the discussion introduces two aspects referred to as “PAM in the cloud” and “PAM for the cloud”.
PAM in the Cloud
The concept of PAM in the cloud refers to running a PAM solution in the cloud as a hosted or Software-as-a-Services (SaaS) solution.
What should you consider when deciding whether to run PAM on-prem or in the cloud?
- Does the vendor’s SaaS product meet your critical use cases?
- Does your organization support a security tool in the cloud?
- Does the solution meet internal cloud governance policies?
- What is the vendor’s data retention and ownership policy?
- What about data encryption in transit and at rest?
- Who provides, and owns the encryption keys?
- Are there network considerations like latency, firewalls, link reliability etc.?
- What are the vendor’s service level agreements (SLA)?
Once you’ve decided on a PAM solution and where it will run (on-prem. or SaaS), it’s time to consider what cloud assets to protect.
Free Workshop:
Privileged Access Management Essentials
Give your team a better understanding of the terms, tools, and strategy for building a successful PAM and IAM program.
PAM for the Cloud
The concept of PAM for the cloud refers to using a PAM solution to manage and secure access to systems and services that reside in the cloud. These services may include the cloud portal itself, servers, storage, databases, applications, networking infrastructure … well you get the idea. Over 90% of companies today have apps and/or infrastructure running in the cloud and these services are often ephemeral (short-lived).
Keep in mind that whether running PAM on-prem. or PAM in the cloud, the discussion of what cloud assets to protect is the same. The challenge is figuring out how to protect what’s running in the cloud.
But why is it challenging?
Most people won’t say it out loud, but security teams are a bit intimidated by the cloud. Sure it’s simple to understand the basics like servers, storage, networking etc., but when people start throwing out words like elastic workloads, s3 buckets, containers, Jenkins, and Kubernetes just to name a few, considering a lower risk 9-to-5 job starts to sound like a great way to go. Don’t give up just yet, because there’s a way to tackle protecting many cloud services.
So how should you approach it?
Start with the things you already know how to protect like cloud directory administrators accounts (think Azure AD), and local Linux/Unix root and Windows administrator accounts. Focus on the more static servers that have relatively long lifecycles in terms of months or years and hold of (for now) on the more ephemeral (short-lived and often changing) workloads. We recommend avoiding an “all or nothing” mentality when tackling PAM for the cloud – to us this seems like straightforward thinking, but you’d be surprised how often organizations are hesitant to start protecting cloud assets when they can’t include “everything” right up front. Remember that protecting some assets is far better than protecting none.
Next limit access to the cloud control panel/portal itself. Portal administrators typically have access to everything, so protecting it is an important initial step.
Now that you’ve protected the privileged access in cloud you already know how to deal with, it’s time to work on governing the ongoing access to various cloud resources as mentioned above. These may include ephemeral server workloads, storage containers, protected file shares, or docker and other containers just to name a few. These may take more time to figure out, and will require assistance from subject matter experts, but once you’ve got it the principles are the same.
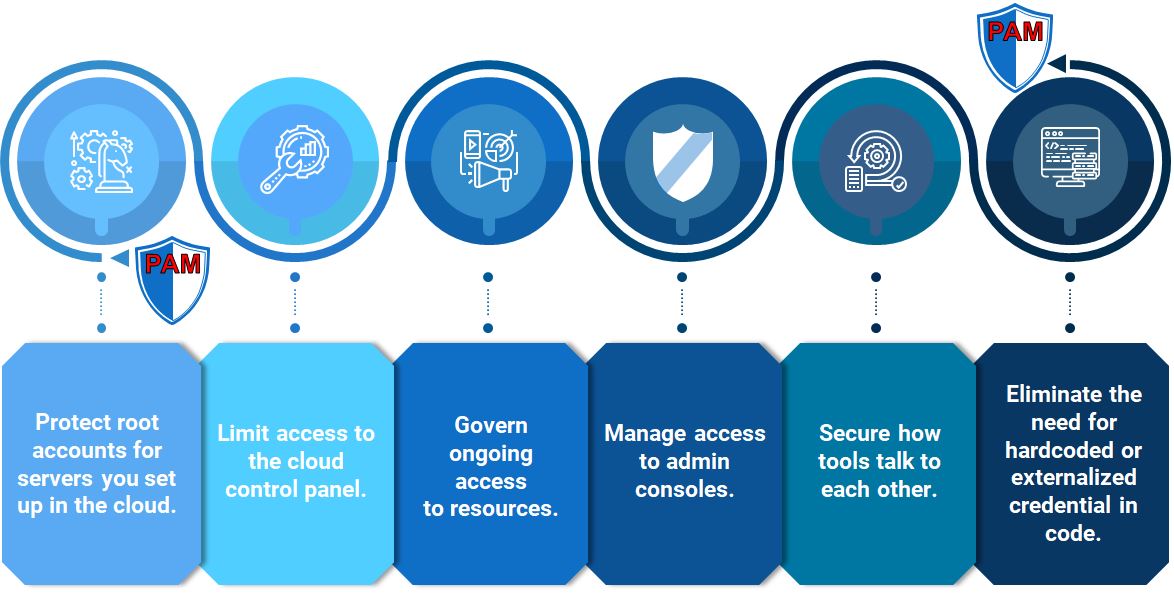
Here a few important cloud areas to consider when protecting privileged cloud access:
- Protect root/admin accounts for servers running in the cloud
- Limit access to the cloud control panel/portal
- Govern ongoing access to resources
- Manage access to admin consoles
- Secure how tools talk to each other
- Vault secrets used within DevOps and CI/CD pipelines
In addition to following these steps, it’s important to consider the organizational change component of PAM for the cloud. Be sure to keep open communication with stakeholders to avoid surprises. Include cloud team managers, and administrators, testing, and DevSecOps teams. Persuade people to your cause through education and partnership. It may take longer to get there, but it’s well worth the effort.
At the end of the day, it’s about applying the privilege access management principles you already know to secure credentials in the cloud. Whether PAM runs in the cloud, or on-prem. The focus should be on eliminating the need for administrators to manage credentials. Ensure that secrets are held under tight control in a central, secure vault. Configure SaaS systems to fetch credentials from the vault. This approach allows users can continue using the SaaS tools they need to achieve business objectives, while security and IT teams have total visibility and control in protecting the organization by enforcing consistent security policies.
How can Integral Partners Help?
As trusted partner of leading PAM tools CyberArk and BeyondTrust, we have deep experience helping organizations implement and maximize Privileged Access Management solutions in the Cloud. Whether you’re early in your journey and need help choosing the right solutions and building a roadmap, or you’re more mature and need help maturing your program and moving to the Cloud, we can help.
- PAM Strategy & Roadmap
What should it look like? What influences it? What first? How do you get there?
- Program Evaluation
Evaluate your PAM or IAM program maturity and assess how you can further reduce risk
- PAM Integrations
It’s often a good idea to integrate your PAM program under your Governance umbrella. We can help evaluate if that makes sense for you and help if you decide to integrate - Deciphering the PAM Magic Quadrant
Choosing the right tool in incredibly important but hard to do. Just because a vendor is a “leader” doesn’t mean they’re right for your use case. We’re experts and will give vendor-agnostic advice. - The Cloud & PAM
As outlined in this article, the cloud can complicate your PAM challenges. A big part of our work is helping organizations address those challenges and create a successful PAM program.
If you’re interested in learning more, feel free to put 15 minutes on our calendar here. We’d be happy to help.
You can also find more information here about our very popular free PAM Essentials Workshop: Privileged Access Management Workshop
CASE STUDY
Building Biogen’s PAM Program
Working with Integral Partners, Biogen has been able to implement a new PAM solution that is PAM GxP certified, while increasing the scale and scope of their PAM program.


Comments are closed.