Our PAM Services Protect Your Organization’s Highest-Risk Accounts
Privileged Access Management (PAM) helps ensure that only the users who need it (and only when they need it) have access to your organization’s most sensitive networks, systems, applications, and data. We’ve designed our PAM services and solutions to keep your organization safe from the risk of compliance violations, privacy breaches, and fraud, and eliminate the threat of compromised accounts.
We apply decades of experience to help you customize an implementation to your architectural requirements, integrate a holistic methodology into your operations, and develop a framework for investment prioritization. We’ll give you the tools you need to centrally manage privileged access, including:
⦿ Lockdown credentials (passwords/SSH keys)
⦿ Session isolation, control, and recording
⦿ Monitoring of privileged account usage
⦿ Integration with your security analytics and IGA solutions
⦿ Help with Vendor evaluation
⦿ Comprehensive user training and world-class support

Individual PAM Services
Cloud Privileged Access Management
We can help you protect your privileged accounts in the cloud
Onboarding, Secrets, Third Party Access…
Get visibility into your accounts, give vendor access, and manage credentials.
Featured Platforms

CyberArk records and monitors sessions to protect sensitive information and systems, helping meet audit and compliance requirements.

BeyondTrust offers a flexible design that simplifies integrations, enhances user productivity, and maximizes IT and security investments.

Thycotic has a place in Gartner’s 2021 Magic Quadrant for Privileged Access Management based on its ability to execute and its completeness of vision.

Saviynt, traditionally an IGA platform, also offers PAM functionality. If you’re already a Saviynt customer, their PAM solution is worth considering.
Privileged Access Management
Free PAM Essentials Workshops
Customized PAM workshop – tailored to fit your areas of interest
By far the biggest concern we encounter regarding PAM is that “We don’t know what we don’t know!” Security teams struggle to scope PAM implementations because they’re unable to discover the reality of their environment. They often don’t even know where to start. This free workshop is designed to teach Privileged Access Management concepts, tools, and how it fits into the larger IAM ecosystem. It will also cover what a PAM roadmap looks like and what it takes to build one.
⦿ PAM best practices
⦿ Auditing – Learn how to identify gaps that need attention
⦿ The PAM drive chain & maturity curve
⦿ Recommended PAM roadmap
⦿ Where should PAM reside within your organization?

Privileged Access Management
PAM Vendor Selection
Expert (tool agnostic) insight to help you decipher the PAM magic quadrant and choose PAM platform for you
Every PAM vendor has strengths and weaknesses. To make smart purchasing decisions, you need to fully understand your requirements, your environment, and which vendors and solutions will be a good fit. We pay attention to the vendor marketplace and build a deep understanding of available features and functionality.
We can provide unbiased recommendations and help you make the right decisions.
CLICK HERE to read our “CyberArk vs BeyondTrust Comparison”
Privileged Access Management
PAM Architecture and Deployment
Deploy and operate your PAM platform with confidence
Whether you’ve purchased a solution and want to ensure it’s properly deployed, or you can’t decide which modules you need to maximize the product’s value, we can help.
From designing an RFP to architecting the solution, our experts know how to effectively gather requirements, select the right add-ons, and plan a phased deployment. Then we help you stand it up—architecting a fail-safe configuration and deployment, even in complex environments. Our professional advisors specialize not just in implementations but operations: turning on functionality, running IGA systems, automating onboarding, building out integrations, and factoring in secrets, bots, and DevOps.
Case Study:
Getting Biogen on Track for PAM Maturity
How Integral Partners deployed a new BeyondTrust PAM solution and set the global pharmaceutical giant on the path to GxP

Privileged Access Management
Cloud Privileged Access Management
We can help you protect your privileged accounts in the cloud
The cloud introduces new attack vectors that traditional PAM approaches often struggle to adequately address. As Gartner puts it, the proliferation of privileged accounts and credentials in the cloud is unmanageable without processes and tools. Integral Partners can help you chose the right PAM tools and secure your credentials in the cloud.
⦿ Protect cloud directory administrators accounts (like Azure AD)
⦿ Secure local Linux/Unix root and Windows administrator accounts
⦿ Limit access to your cloud control panel/portal
⦿ Secure how your cloud tools talk to each other
⦿ Protect vault secrets used within DevOps and CI/CD pipelines
Privileged Access Management
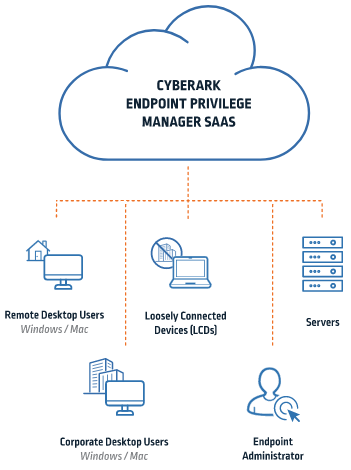
Endpoint Privileged Management
Protect endpoints while securely giving users access to what they need
Workstations are a key target of hackers looking to gain access to your network. Removing local admin rights manually will significantly reduce risk, but can also overwhelm your IT department with install, configuration and support requests. It will also lead to very unhappy users.
By using Endpoint Privileged Management, we can remove admin access while still allowing the trusted applications your users need to run. EPM application control will block and contain malicious software at the endpoints, preventing ransomware and other security threats. You’ll also have the ability to grant time-based user access and user elevation. To further protect your data, Privileged Deception will allow your security teams to create credential lures for attackers, and prevent them from reaching actual targets.
Got Shelfware?
We can help you maximize the value of your PAM tools
One of the most common requests we get is helping organizations who have a PAM tool but aren’t sure how to move forward. We can help bring clarity to your program and map out a successful strategy.
Privileged Account Onboarding
Get visibility into all your accounts
With the growth of DevOps and bots, privileged account onboarding is a popular solution. Let us help you root out costly errors, like over-privileged accounts and unencrypted passwords. We can move your application service accounts from scripts to a secure vault in your PAM solution, and set up session monitoring for privileged users.
Third Party Access
Give vendors secure, automated access
Third parties such as vendors, suppliers, partners, and contractors often need access to solutions inside a company’s network. Yet this access exposes companies to all sorts of threats. We can solve the problem of vendor access by allowing companies to receive third-party requests, grant temporary access, allow approved functions, and then revoke access, with no exchanges of passwords.
Privileged Secrets
Manage credentials securely at DevOps speed
DevOps practices can reveal vulnerabilities in PAM security, but many PAM solutions aren’t designed to support the scale and speed of DevOps functions. DevOps engineers often embed passwords and other credentials right into the scripts for containers, servers, and apps like Chef, Puppet, and Jenkins. We’ll help you establish PAM vaults to ensure secrets are automatically coded, stored, managed, and rotated.
Getting Biogen on Track for PAM Maturity
Biogen, one the world’s leading pharmaceutical firms, recognized several ways they needed to improve their Privileged Access Management (PAM) maturity in order to effectively align with PAM Good Practices (GxP) for the Biotechnology industry.
Working with Integral Partners, Biogen has been able to implement a new PAM solution that is PAM GxP certified while increasing the scale and scope of their PAM program—making the company more secure while establishing the basis for even greater PAM capabilities in the future.
Vertical
Biotechnology
IAM Technology
Privileged Access Management
Solution
Migrate legacy system
Elevate PAM maturity
Follow GxP guidelines
Why Integral Partners can help with your PAM program
We focus exclusively on IAM. It’s all we do. We can deliver the results you need, on time and in budget. You get high-touch guidance, quick answers, and access to our deep base of expertise.
- We’re trusted partners with all leading vendors but tool agnostic
- We have over 20 years of experience with IAM and PAM
- We can help – from strategy, evaluation, purchase, implementation and support
Want to learn more? Schedule a quick conversation with one of our PAM experts. They can answer any initial PAM questions you have or other IAM related issues.
Use this form to reach out and get started.


